生成apiserver证书!
vim ca-csr.json
{ "CN": "kubernetes", "key": { "algo": "rsa", "size": 2048
}, "names": [
{ "C": "CN", "L": "BeiJing", "ST": "BeiJing", "O": "k8s", "OU": "System"
}
]
}vim ca-config.json
{ "signing": { "default": { "expiry": "876000h"
}, "profiles": { "kubernetes": { "expiry": "876000h", "usages": [ "signing", "key encipherment", "server auth", "client auth"
]
}
}
}
}创建CA配置json文件
创建apiserver证书的所需配置文件
vim kube-proxy-csr.json
{ "CN": "system:kube-proxy", "hosts": [], "key": { "algo": "rsa", "size": 2048
}, "names": [
{ "C": "CN", "L": "BeiJing", "ST": "BeiJing", "O": "k8s", "OU": "System"
}
]
}
vim server-csr.json
{ "CN": "kubernetes", "hosts": [ "10.0.0.1", "127.0.0.1", "kubernetes", "kubernetes.default", "kubernetes.default.svc", "kubernetes.default.svc.cluster", "kubernetes.default.svc.cluster.local", "10.100.97.55", "10.100.97.78", "10.100.97.79", "10.100.97.80", "10.100.97.81", "10.100.97.82", "10.100.97.83"
], "key": { "algo": "rsa", "size": 2048
}, "names": [
{ "C": "CN", "L": "BeiJing", "ST": "BeiJing", "O": "k8s", "OU": "System"
}
]
}.
├── ca-config.json
├── ca-csr.json
├── kube-proxy-csr.json
└── server-csr.json
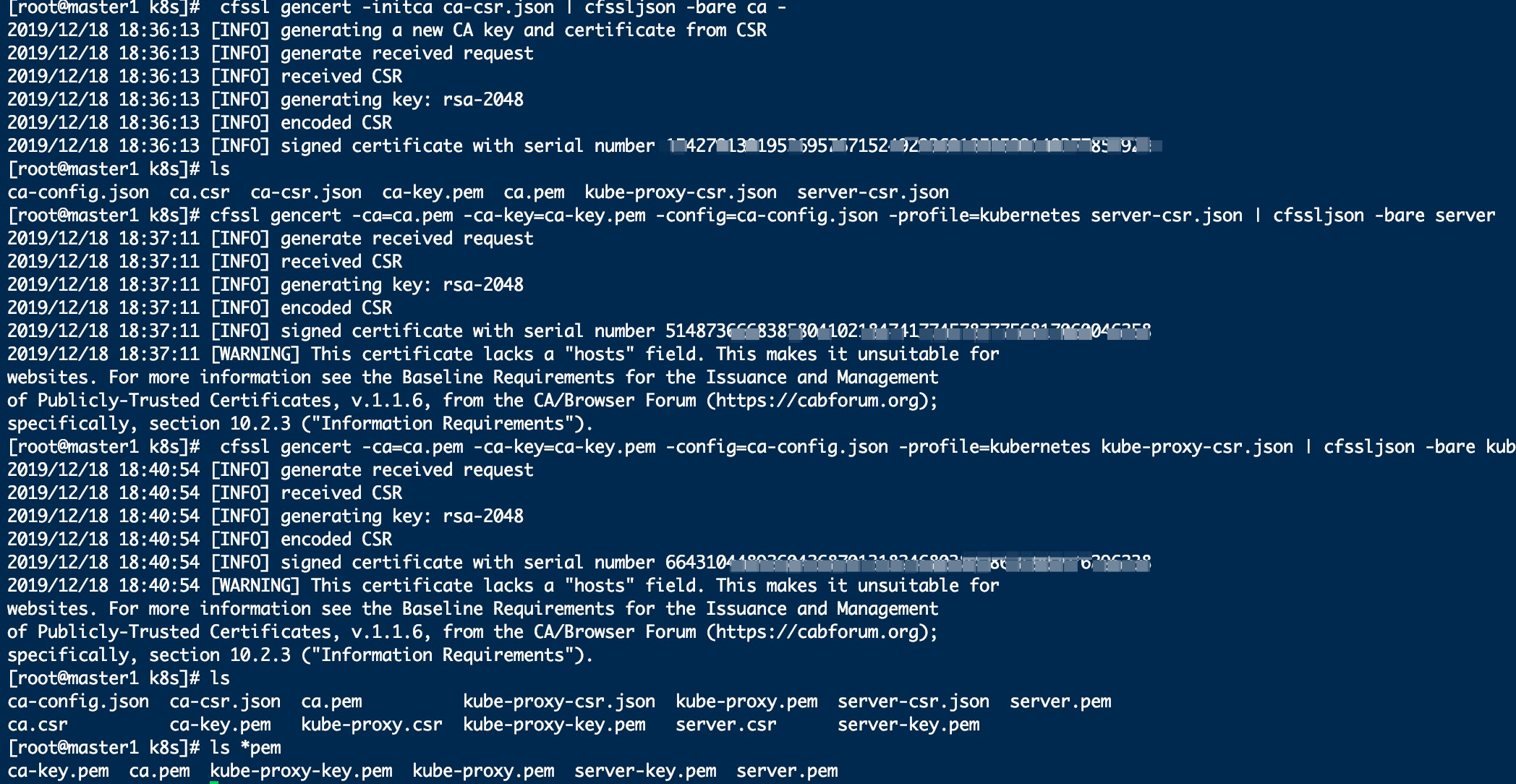
生产证书
cfssl gencert -initca ca-csr.json | cfssljson -bare ca - cfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes server-csr.json | cfssljson -bare servercfssl gencert -ca=ca.pem -ca-key=ca-key.pem -config=ca-config.json -profile=kubernetes kube-proxy-csr.json | cfssljson -bare kube-proxy
部署master
二进制包下载地址:https://github.com/kubernetes/kubernetes/blob/master/CHANGELOG-1.16.md#v1161
mkdir -p /opt/kubernetes/{bin,cfg,k8s,ssl}
wget "https://dl.k8s.io/v1.16.1/kubernetes-server-linux-amd64.tar.gz"tar xvf kubernetes-server-linux-amd64.tar.gz
cp *.pem /opt/kubernetes/ssl/cp /usr/local/src/kubernetes/server/bin/{kube-apiserver,kube-controller-manager,kube-scheduler,kubectl} /opt/kubernetes/bin/二进制文件位置:kubernetes/server/bin
创建配置文件 /opt/kubernetes/cfg/ ##### vim kube-apiserver.conf KUBE_APISERVER_OPTS="--logtostderr=false \ --v=2 \--log-dir=/opt/kubernetes/logs \--etcd-servers=https://10.100.97.78:2379,https://10.100.97.79:2379,https://10.100.97.55:2379 \--bind-address=10.100.97.78 \--secure-port=6443 \--advertise-address=10.100.97.78 \--allow-privileged=true \--service-cluster-ip-range=10.0.0.0/24 \--enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction \--authorization-mode=RBAC,Node \--enable-bootstrap-token-auth=true \--token-auth-file=/opt/kubernetes/cfg/token.csv \--service-node-port-range=30000-32767 \--kubelet-client-certificate=/opt/kubernetes/ssl/server.pem \--kubelet-client-key=/opt/kubernetes/ssl/server-key.pem \--tls-cert-file=/opt/kubernetes/ssl/server.pem \--tls-private-key-file=/opt/kubernetes/ssl/server-key.pem \--client-ca-file=/opt/kubernetes/ssl/ca.pem \--service-account-key-file=/opt/kubernetes/ssl/ca-key.pem \--etcd-cafile=/opt/etcd/ssl/ca.pem \--etcd-certfile=/opt/etcd/ssl/server.pem \--etcd-keyfile=/opt/etcd/ssl/server-key.pem \--audit-log-maxage=30 \--audit-log-maxbackup=3 \--audit-log-maxsize=100 \--audit-log-path=/opt/kubernetes/logs/k8s-audit.log"##### vim kube-controller-manager.conf KUBE_CONTROLLER_MANAGER_OPTS="--logtostderr=false \ --v=2 \--log-dir=/opt/kubernetes/logs \--leader-elect=true \--master=127.0.0.1:8080 \--address=127.0.0.1 \--allocate-node-cidrs=true \--cluster-cidr=192.244.0.0/16 \--service-cluster-ip-range=192.0.0.0/24 \--cluster-signing-cert-file=/opt/kubernetes/ssl/ca.pem \--cluster-signing-key-file=/opt/kubernetes/ssl/ca-key.pem \--root-ca-file=/opt/kubernetes/ssl/ca.pem \--service-account-private-key-file=/opt/kubernetes/ssl/ca-key.pem \--experimental-cluster-signing-duration=87600h0m0s"##### vim kube-scheduler.conf KUBE_SCHEDULER_OPTS="--logtostderr=false \ --v=2 \--log-dir=/opt/kubernetes/logs \--leader-elect \--master=127.0.0.1:8080 \--address=127.0.0.1"
创建启动文件到/usr/lib/systemd/system
##########cat kube-apiserver.service [Unit] Description=Kubernetes API Server Documentation=https://github.com/kubernetes/kubernetes[Service] EnvironmentFile=/opt/kubernetes/cfg/kube-apiserver.conf ExecStart=/opt/kubernetes/bin/kube-apiserver $KUBE_APISERVER_OPTS Restart=on-failure [Install] WantedBy=multi-user.target ###################### cat kube-controller-manager.service [Unit] Description=Kubernetes Controller Manager Documentation=https://github.com/kubernetes/kubernetes[Service] EnvironmentFile=/opt/kubernetes/cfg/kube-controller-manager.conf ExecStart=/opt/kubernetes/bin/kube-controller-manager $KUBE_CONTROLLER_MANAGER_OPTS Restart=on-failure [Install] WantedBy=multi-user.target ######################## cat kube-scheduler.service [Unit] Description=Kubernetes Scheduler Documentation=https://github.com/kubernetes/kubernetes[Service] EnvironmentFile=/opt/kubernetes/cfg/kube-scheduler.conf ExecStart=/opt/kubernetes/bin/kube-scheduler $KUBE_SCHEDULER_OPTS Restart=on-failure [Install] WantedBy=multi-user.target ###############
启用TLS Bootstrapping
vim /opt/kubernetes/cfg/token.csv
[root@master1 cfg]# tree /opt/kubernetes/ ├── bin │ ├── kube-apiserver │ ├── kube-controller-manager │ ├── kubectl │ └── kube-scheduler ├── cfg │ ├── kube-apiserver.conf │ ├── kube-controller-manager.conf │ ├── kube-scheduler.conf │ └── token.csv ├── k8s └── ssl ├── ca-key.pem ├── ca.pem ├── kube-proxy-key.pem ├── kube-proxy.pem ├── server-key.pem └── server.pem##################手动启动可以检测参数是否有错误 /opt/kubernetes/bin/kube-apiserver --logtostderr=true --v=2 --log-dir=/opt/kubernetes/logs --etcd-servers=https://10.100.97.78:2379,https://10.100.97.79:2379,https://10.100.97.55:2379 --bind-address=10.100.97.78 --secure-port=6443 --advertise-address=10.100.97.78 --allow-privileged=true --service-cluster-ip-range=10.0.0.0/24 --enable-admission-plugins=NamespaceLifecycle,LimitRanger,ServiceAccount,ResourceQuota,NodeRestriction --authorization-mode=RBAC,Node --enable-bootstrap-token-auth=true --token-auth-file=/opt/kubernetes/cfg/token.csv --service-node-port-range=30000-32767 --kubelet-client-certificate=/opt/kubernetes/ssl/server.pem --kubelet-client-key=/opt/kubernetes/ssl/server-key.pem --tls-cert-file=/opt/kubernetes/ssl/server.pem --tls-private-key-file=/opt/kubernetes/ssl/server-key.pem --client-ca-file=/opt/kubernetes/ssl/ca.pem --service-account-key-file=/opt/kubernetes/ssl/ca-key.pem --etcd-cafile=/opt/etcd/ssl/ca.pem --etcd-certfile=/opt/etcd/ssl/server.pem --etcd-keyfile=/opt/etcd/ssl/server-key.pem --audit-log-maxage=30 --audit-log-maxbackup=3 --audit-log-maxsize=100 --audit-log-path=/opt/kubernetes/logs/k8s-audit.log
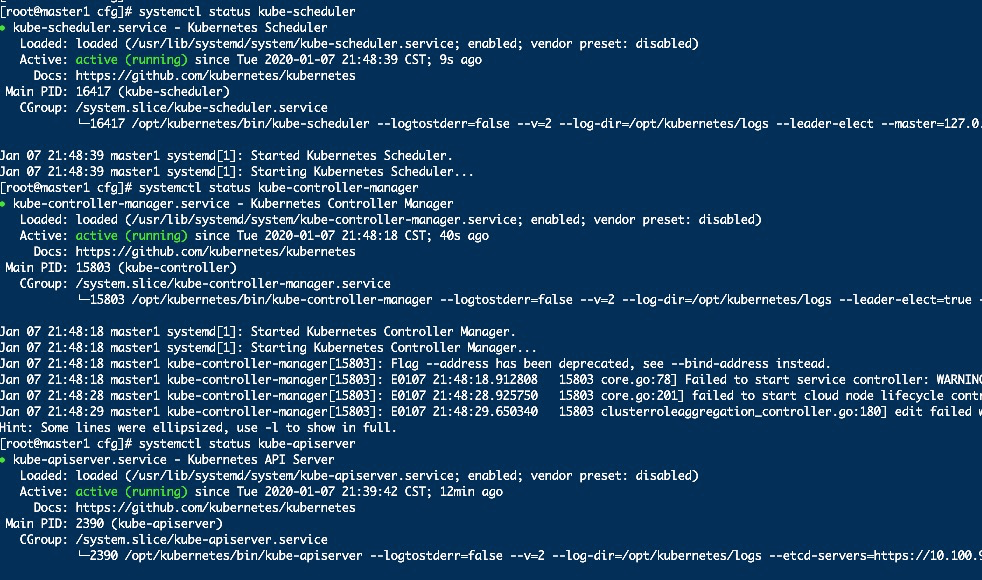
systemctl start kube-apiserver
systemctl start kube-controller-manager
systemctl start kube-scheduler
systemctl enable kube-apiserver
systemctl enable kube-controller-manager
systemctl enable kube-scheduler